Preface
pfSense configuration to allow inbound traffic for internet connection in client-side and also implement a remote site
As a Firewall pfSense will be block all connection in LAN interface, except it’s web configuration :xD (because it’s directly connected to pfSense)
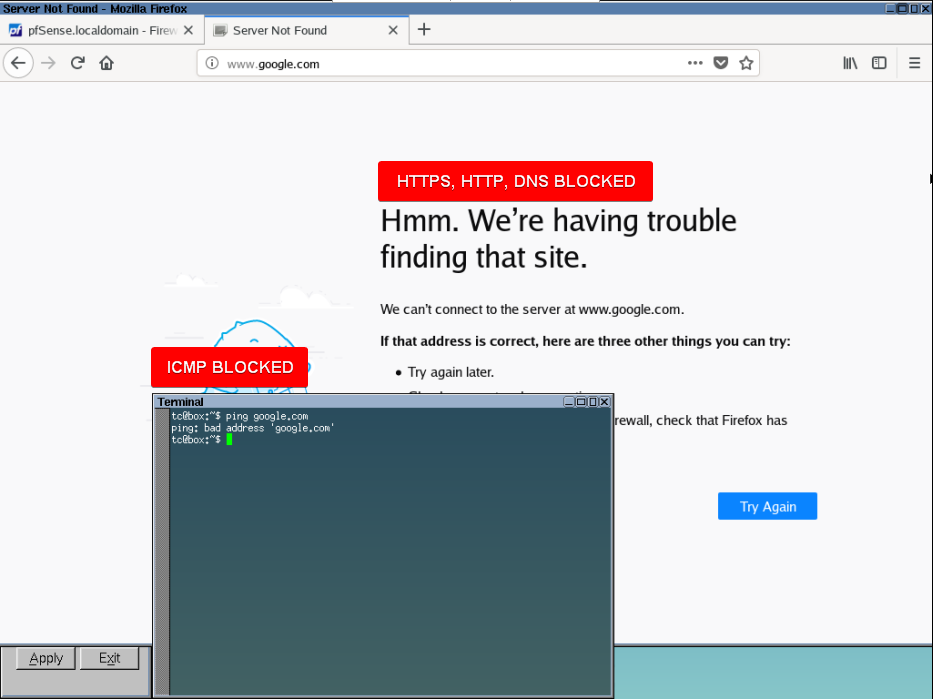
Also his block all traffic comes from WAN interface. So if you ping pfSense from WAN interface you get 100% packet loss :v.
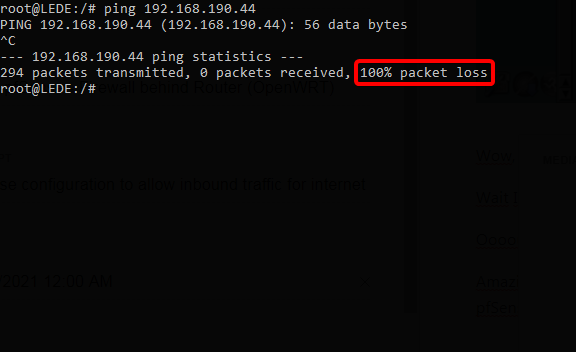
Lab Actually
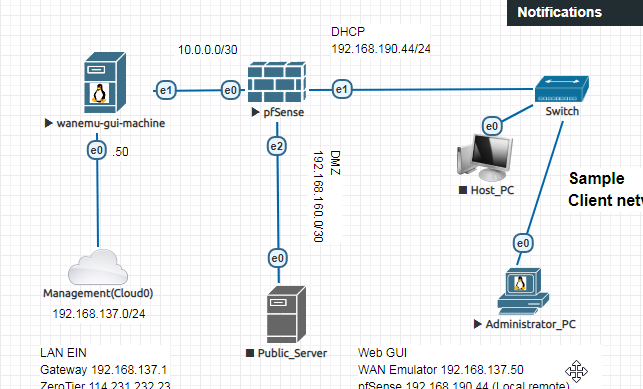
Prerequisite: Connecting Firewall to the internet
To do this, OpenWRT must be configured such as intial config, static route (to client-side), default route (internet), setup Firewall Zones and PortForward Firewall rules.
pfSense too, it’s need to configure basic things like LAN/WAN/OPT1 interface and default gateway.
and don’t forget to set up DNS in General setup! and DNS resolver like 8.8.8.8 with 8.8.4.4 or 1.1.1.1 with 1.0.0.1
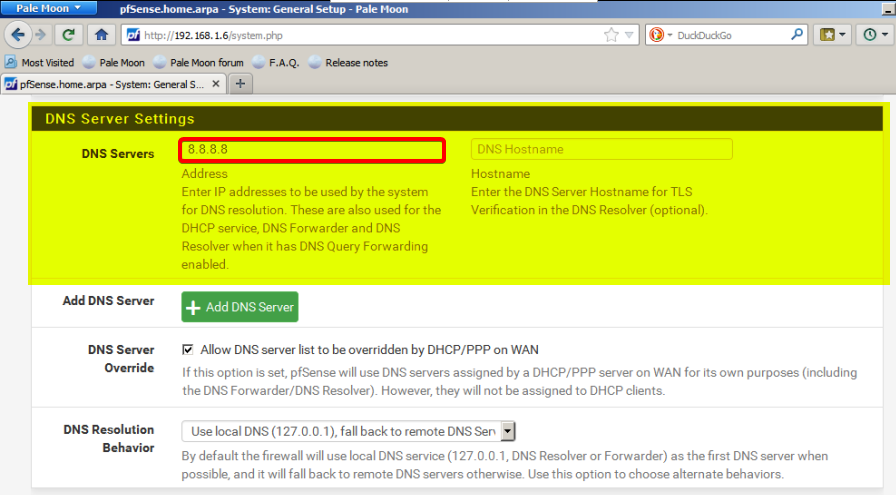
maybe, thats all requirements.
So, to connecting pfSense to the internet behind router…. The thing is ‘firewall setting’ in the router.
It should be assign to allow inbound traffic (traffic came from internet).
Look at this how to! After OpenWRT. I will give an example for another router vendor a.k.a Cisco.
OpenWRT: Configure Zones (interface) Firewall
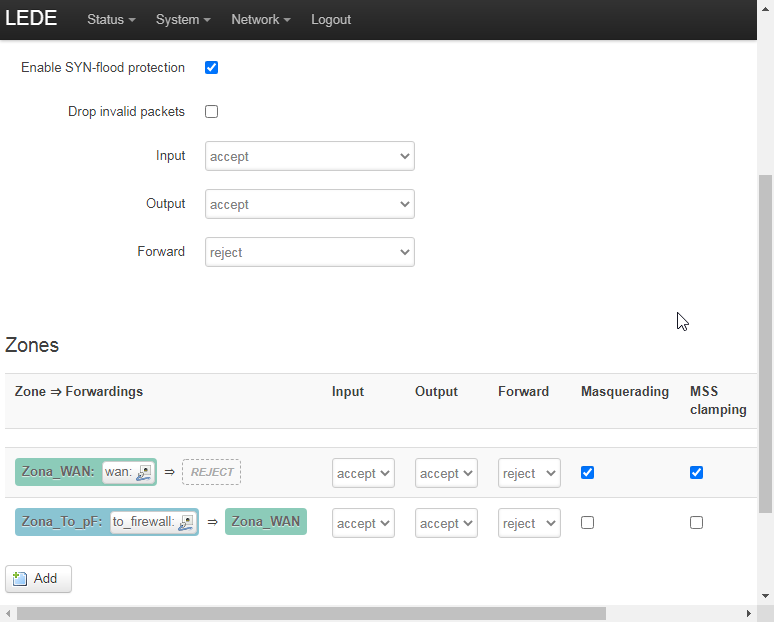
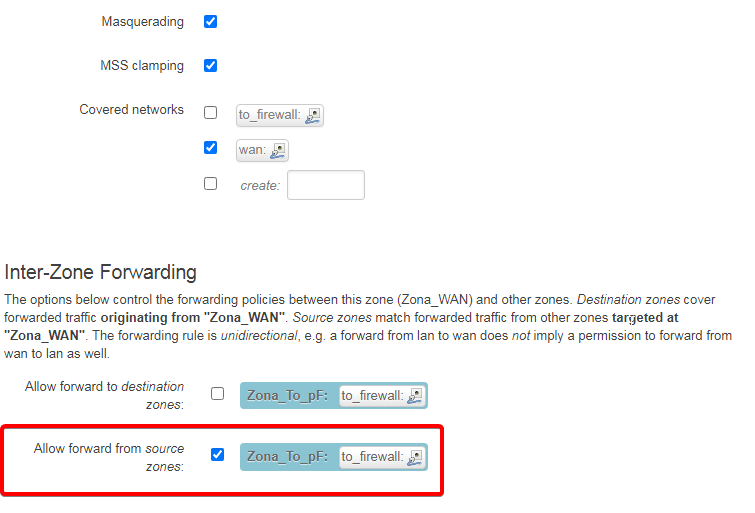
WAN interface (Zona_WAN) must be Masquarade and the Source zones match forwarded traffic from other zones
WAN interface’s source zone targeted at “Zona to_pF”
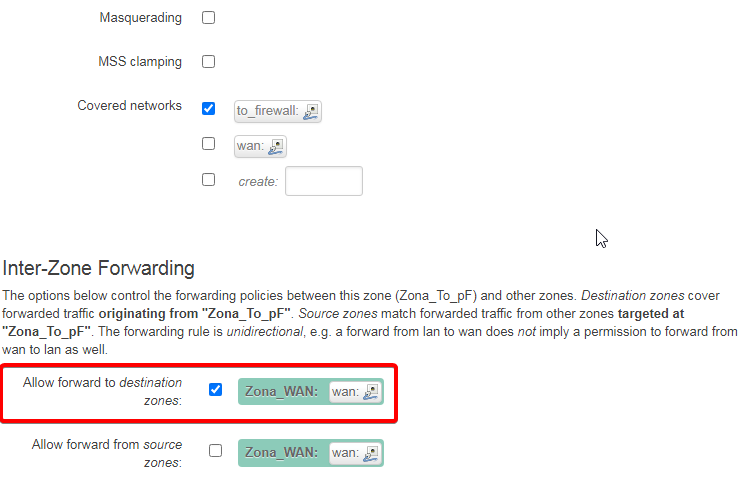
And then, LAN interface (Zona to_pF) must be setup for Destination zones match forwarded traffic from other zones.
LAN interface’s destination zones targeted at “Zona_WAN”
OpenWRT: Configure Port Forwards Firewall
So, after that the physical interface LAN (Zone to_pF) is interface as pfSense gateway to be Remote Access or allows remote computers on the Internet/external network to be remoted pfSense or client host.
To do this, it’s need to be allow IPv4-tcp, udp, icmp from any host or ip address in the internet Via any routers or gateway. This is how gonna be look at.
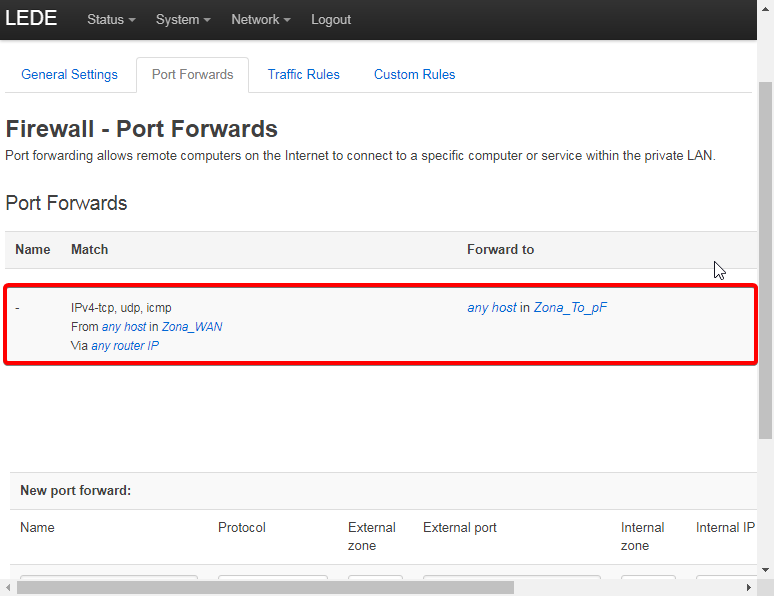
It’s done! don’t forget to enable OpenWRT firewall at System>Startup.
And let’s see..
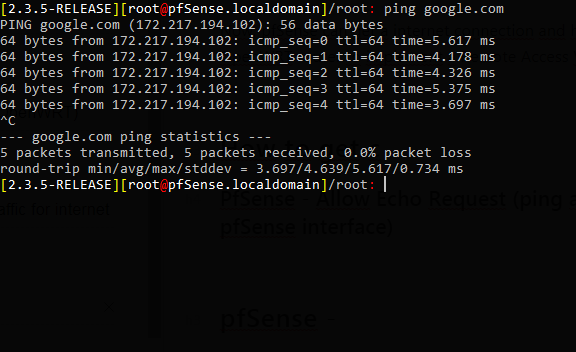
Now I’m clear with prerequisite, my pfSense can get a internet connection and have an access from OpenWRT router to implement a Remote Access VPN.
Bonus: How different with Cisco router?
Now, I will show the different firewall configuration in other router vendor, example is Cisco.
This is the example method in Cisco router.
Note:
Inbound traffic is traffic came in from internet or WAN.
Outbound traffic is traffic where come from LAN interface. Such as applications, user or etc.
first, I need set up WAN interface to allow inbound traffic (traffic from internet to local area network)
Router(config)# int fa0/0 Router(config-if)# ip add dhcp Router(config-if)# ip nat outside Router(config-if)# no sh
connecting cisco to the internet (NAT cloud) with default static route and setup custom dns server
Router(config)# ip route 0.0.0.0 0.0.0.0 192.168.89.1
Router(config)# ip name-server 8.8.8.8
Router(config)# ip domain-lookup
WAN interface need to be ruled with nat outside in Cisco. * and configuration for LAN interface and allow outbound (traffic from LAN interface) traffic
Router(config)# int fa0/1
Router(config-if)# ip add 192.168.1.1 255.255.255.0
Router(config-if)# ip nat inside
Router(config-if)# no sh
at LAN interface exactly it need tobe ruled with nat inside * NAT rule statements for LAN interface
Router(config)# ip nat inside source list 1 interface FastEthernet0/0 overload
adding Access-List 1 (This allows the LAN to get connection to the internet). It will be use wilcard mask instead of subnet mask
Router(config)# access-list 1 permit 192.168.1.0 0.0.0.255
In this Cisco router example, now pfSense can perfectly ping to google.com behind Cisco Router.
Next is follow this 2 steps to get and manage internet for client and implement Remote Access.
Step 1: Setup pfSense to allow inbound traffic for client internet connection
I know, In a fact pfSense is a router! But, as a firewall his will block any trafic by default. So, it will be my work to opened just only what I needs.
One of that must be configured or to be opened is client internet connection.
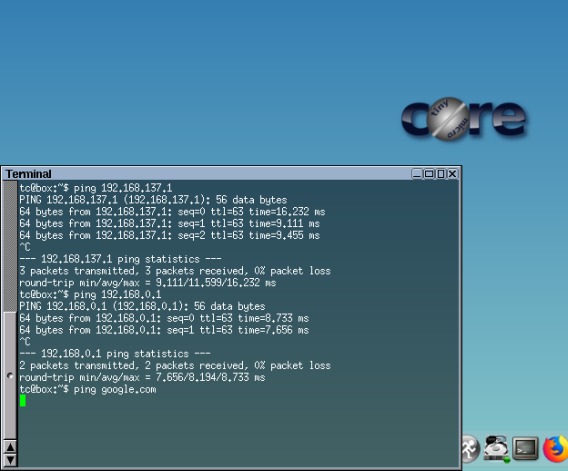
This screenshoot indicate client need to access ICMP Protocol
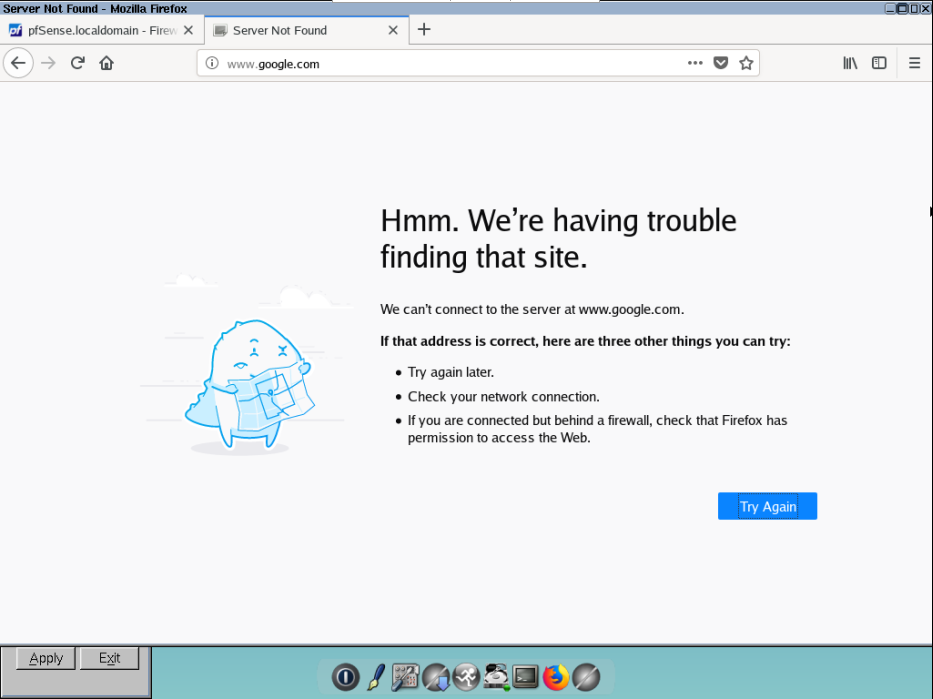
And this screenshoot indicate client need to access DNS (53), HTTP (80), HTTPS (443) port
So, follow this
Create LAN Group Aliases
I recomended to do this because it will be completely easier for manage something for a lots of user in different connection and needs. So, implement a group or Aliases will be simplify your access management :v
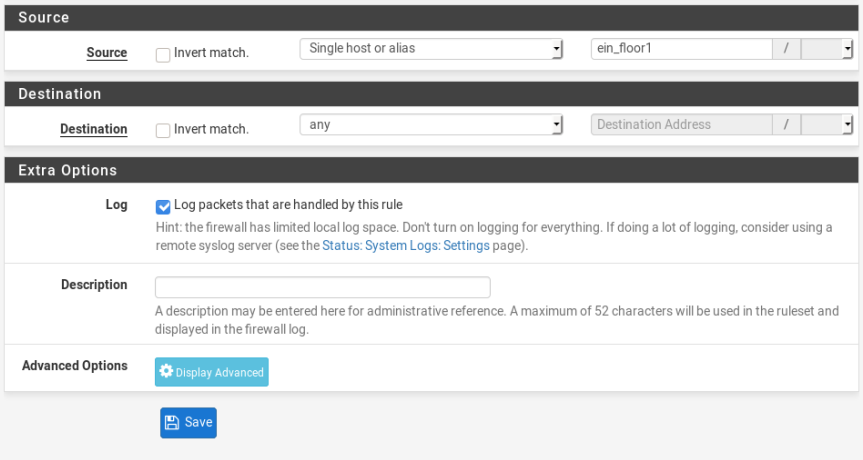
In case rule to allowing internet access (https, http, dns) his need to know who is the man will be applied to this LAN rule (address, group, aliases, or something). This man It’s called Source.
And what is service or port to be asssign in rule. It’s called Destination.
First, I need to be setup Source which is will be grouped in firewall rule as “Alliases”.
It will grouped base on the directly connected port (LAN port/vtnet1)
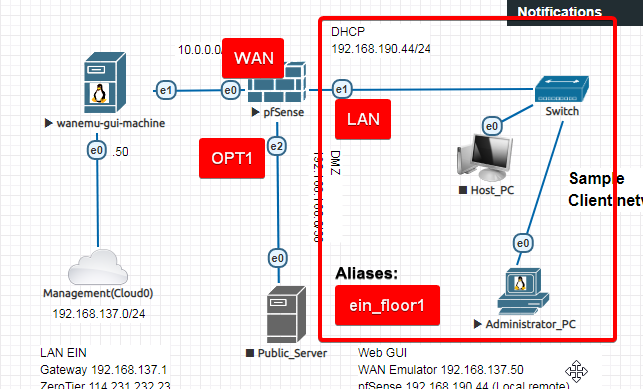
I will create an aliases name: ein_floor1
So, go to Firewall>Aliases>Port and create new aliases with
- “name: ein_floor1”
- “Type: network(s)”
- “Port: vtnet1”
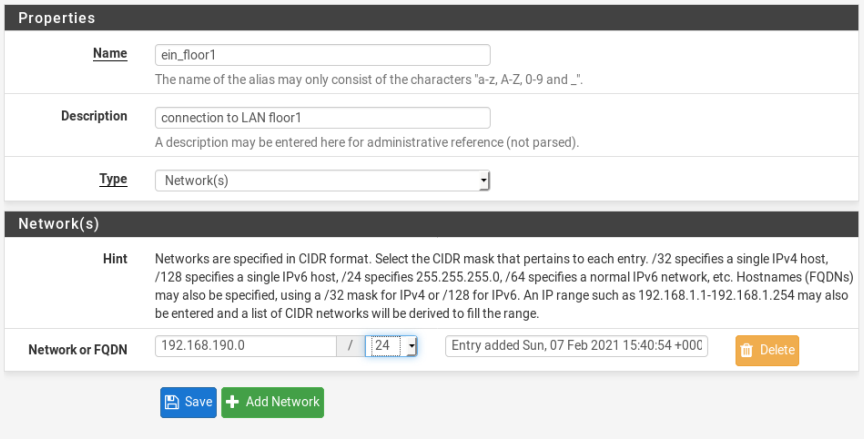
That’s all. Now I have grouped for lan network (192.168.190.0/24)
Create rule (in LAN interface firewall) to allow dns, https and http traffic
Enter Firewall>Rules>LAN menu and create new rules with “action: passed” to allow the spesific traffic, “Interface: LAN”, “Address Family: IPv4” and “protocol: TCP/UDP”.
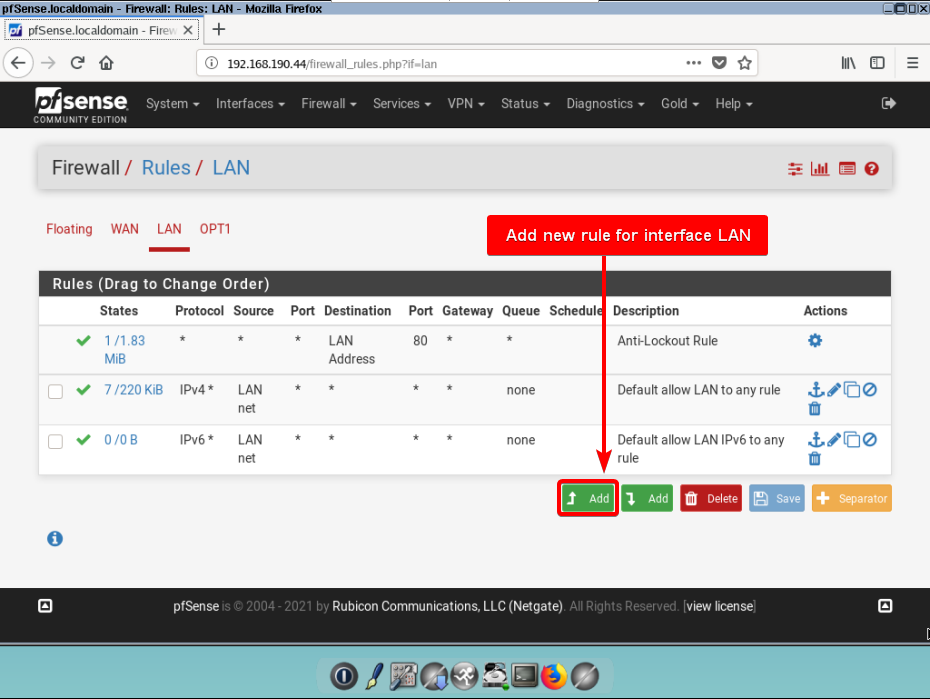
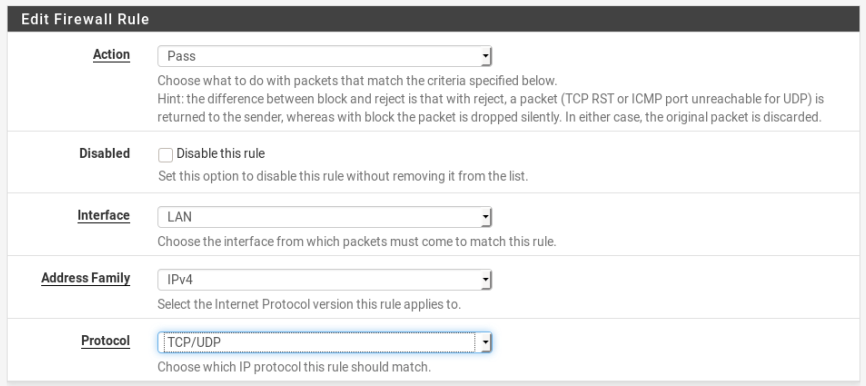
So, first rule to allow DNS
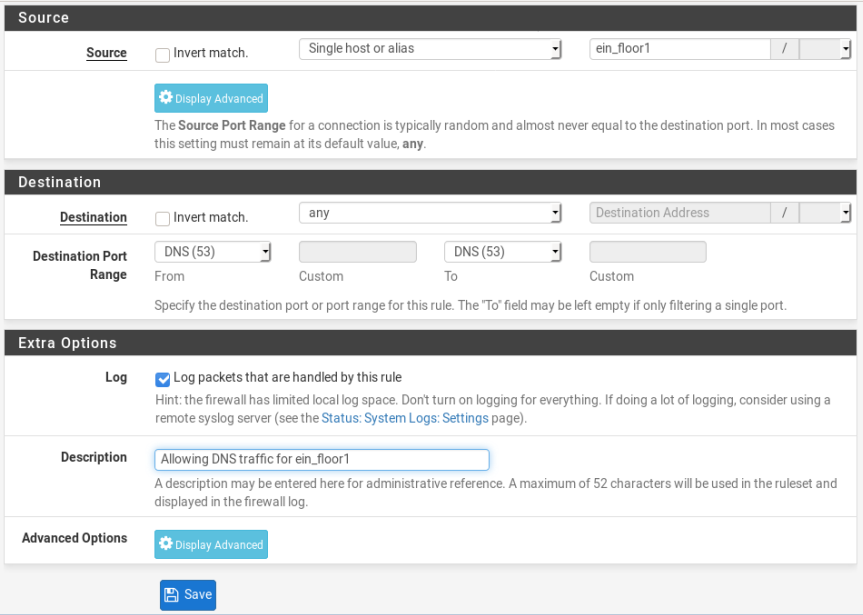
Second, rule to allow HTTPS
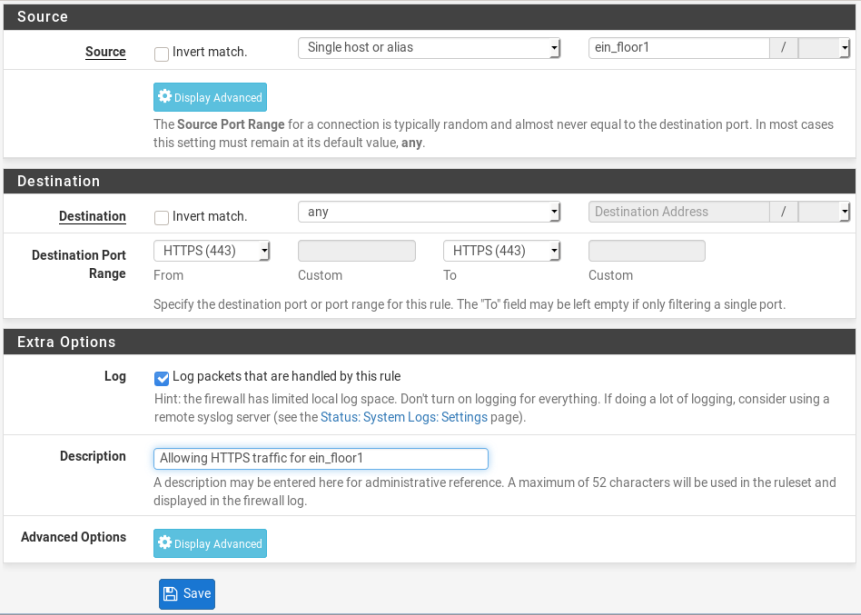
Third, rule to allow HTTP
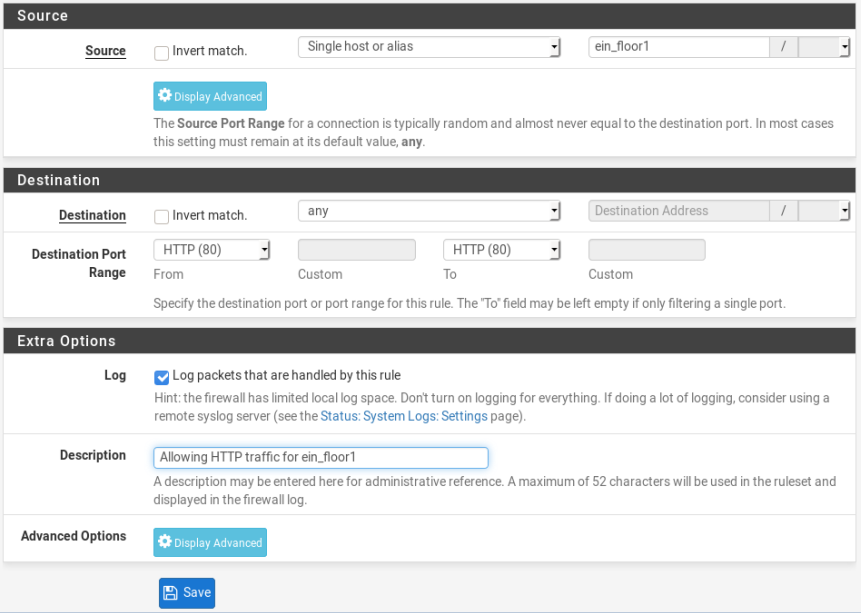
Now, grouped client in LAN network (192.168.190.0/24) can access internet.
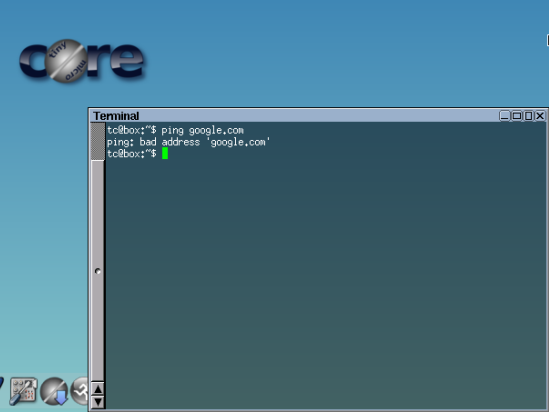
Ouh my god………………………….
Wow, it still not get internet access :v
Wait I must check up …
Oooouh …
Amazing!!! ICMP Protocol not in rule!!! This is why the client still not get the internet access.
Sorry, I’m forget this one haha…
So, lets add rule for WAN interface.
Create rule (in LAN interface firewall) to ICMP Protocol traffic (sorry I’m forgot this)
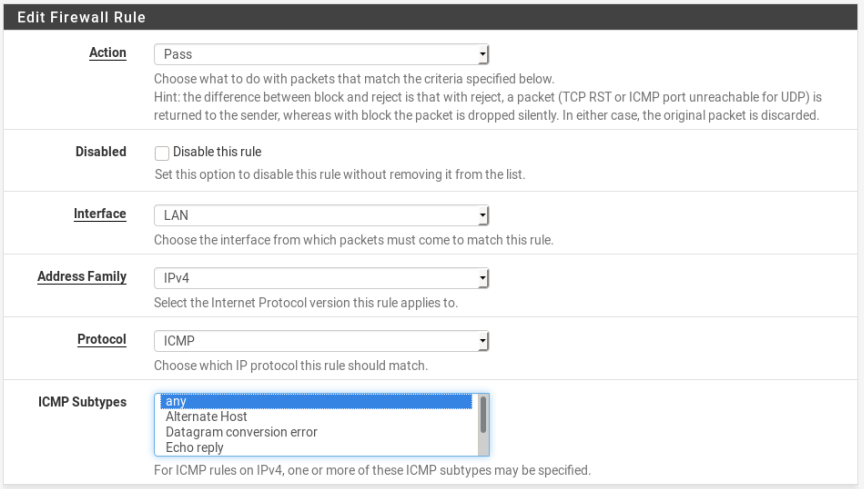
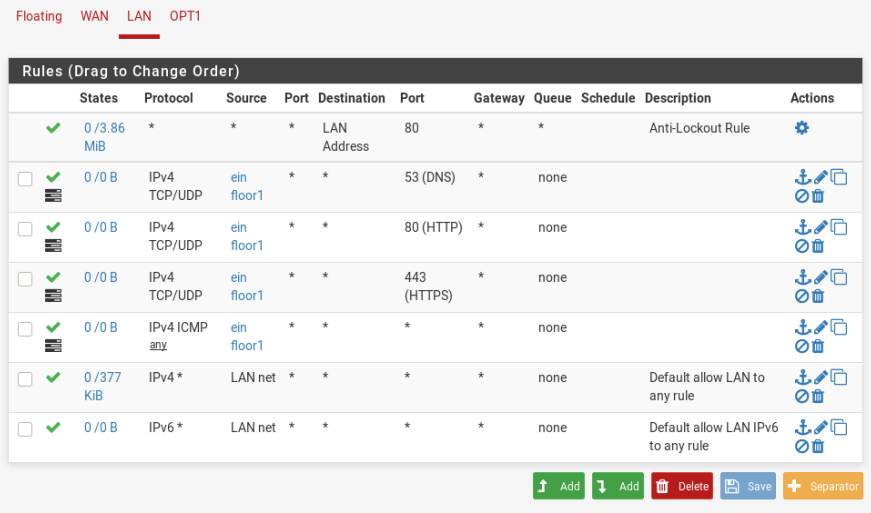
So, in Step 1 (LAN interface rules) we have all this rule.
Step 2: Setup Remote Access in pfSense
As a what i told in beginning. I wanna setup pfSense to be have a connection to external network or internet.